A vulnerability in the HTTP/2 network protocol is currently being exploited, resulting in the largest DDoS attack in history. Find out what security teams should do now, and hear what Cloudflare’s CEO has to say about this DDoS.
Google, AWS and Cloudflare have reported the exploitation of a zero-day vulnerability named HTTP/2 Rapid Reset and tracked as CVE-2023-44487, which is currently used in the wild to run the largest Distributed Denial of Service attack campaigns ever seen. All organizations or individuals using servers that provide HTTP/2 to the internet are vulnerable.
Jump to:
HTTP/2, also known as HTTP/2.0, is a major revision of the HTTP network protocol that is used to transfer data between computers and web servers. HTTP/2 was developed to make web applications faster, as well as more efficient and secure.
A fundamental difference with HTTP/1.1 resides in its multiplexing capabilities. In HTTP/1.1, multiple connections were required for parallel communication, leading to inefficiency and increased latency. HTTP/2 enables multiple requests and responses to be sent and received in parallel over a single TCP connection.
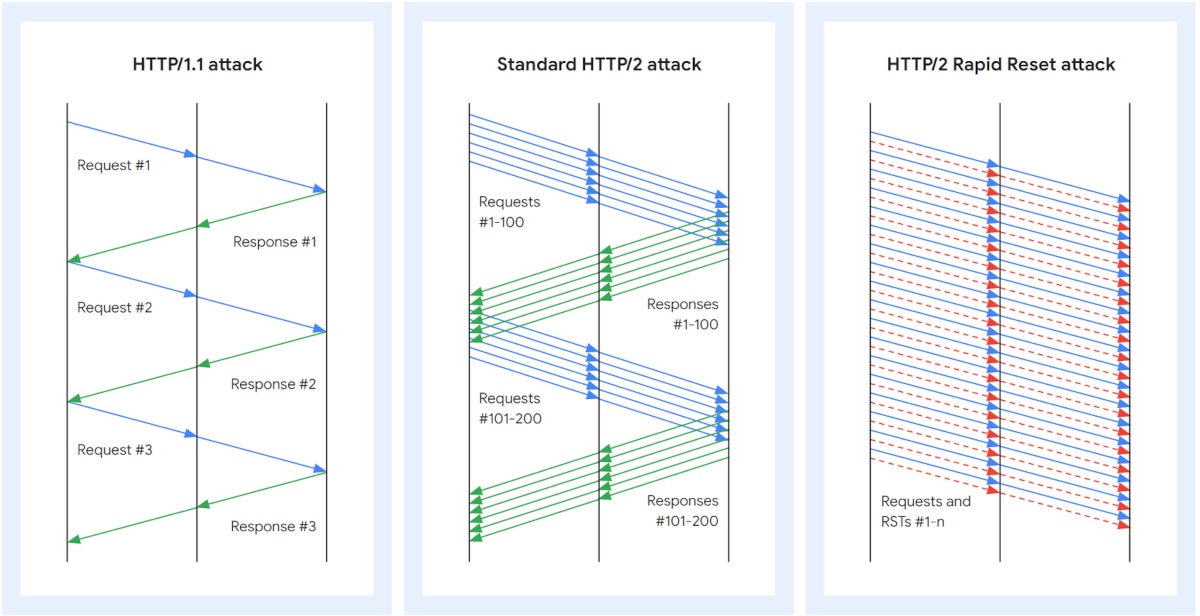
The HTTP/2 Rapid Reset attack works by leveraging HTTP/2’s stream cancellation feature: The attacker sends a request and cancels it immediately.
Automating that process of sending/canceling at scale leads to a DDoS attack, which is what attackers did using multiple bots (Figure A).
Figure A
Amazon observed and mitigated more than a dozen HTTP/2 Rapid Reset attacks over two days in late August, the strongest one hitting its infrastructures at 155 millions of requests per second. Cloudflare reported a peak at 201 million requests per second and mitigated more than 1,100 other attacks with more than 10 million RPS, and 184 attacks greater than the previous DDoS record of 71 million RPS.
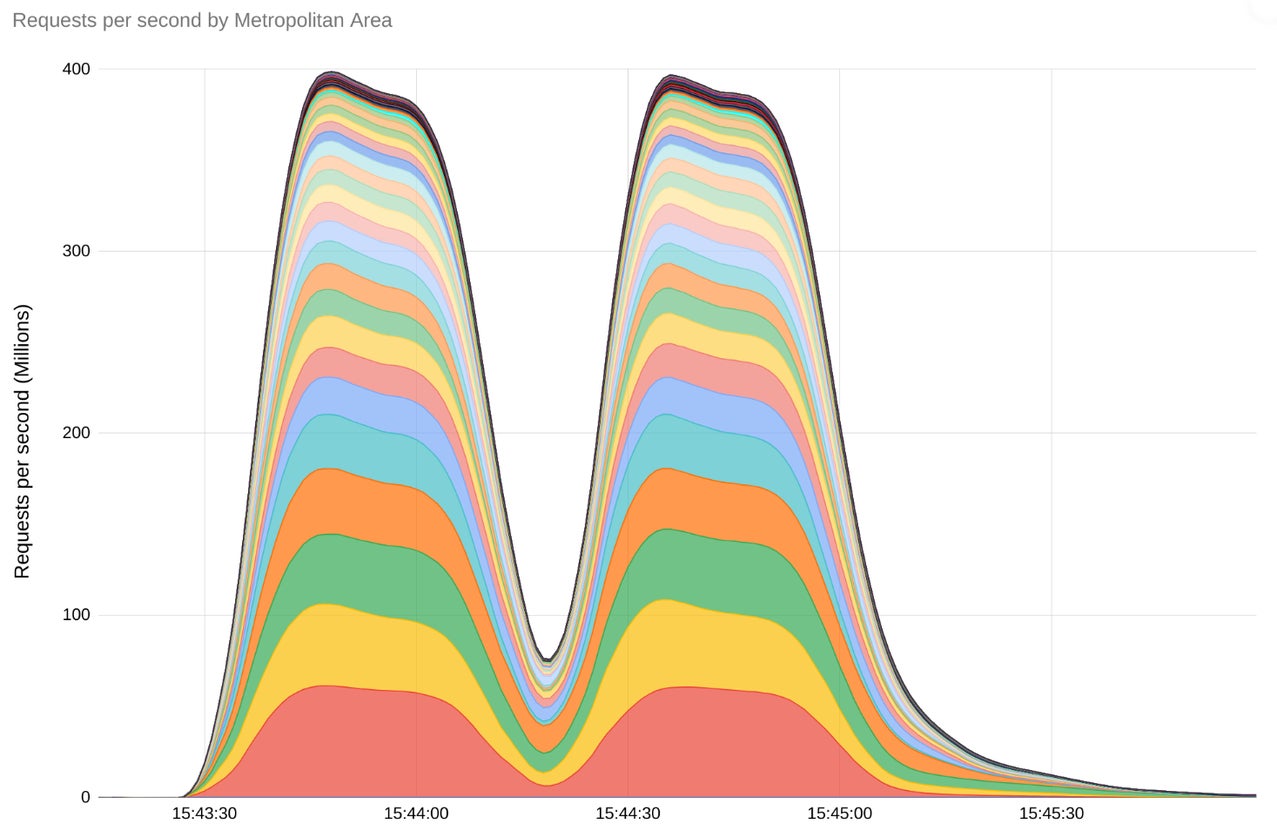
Google reported the biggest attack, which reached a peak of 398 millions RPS using the HTTP/2 Rapid Reset technique (Figure B). As stated by Google in its blog post about the DDoS attack, “For a sense of scale, this two minute attack generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023.”
Figure B
When we asked CloudFlare CEO and co-founder Matthew Prince about the number of bots needed to launch such attacks, he said that it needed, “Between 10,000 – 20,000 nodes in the botnet, which is relatively small. That’s concerning because botnets today with hundreds of thousands or millions of nodes are common. And this attack should scale linearly with the number of nodes in the botnet. It may be possible to generate an attack larger than the estimated legitimate traffic volume of the web (1–3 billion requests per second) but all focused on a single victim. That’s something that even the largest organizations would not be able to handle without appropriate mitigation.”
From another Cloudflare blog post: “Because the attack abuses an underlying weakness in the HTTP/2 protocol, we believe any vendor that has implemented HTTP/2 will be subject to the attack. This included every modern web server.”
Google coordinated a cross-industry response with other cloud providers and software maintainers who implement the HTTP/2 protocol stack. The coordination allowed intelligence sharing and mitigation methodologies in real time as the attacks were ongoing.
Patches and other mitigation techniques emerged from it. From Google’s blog post: “The collaboration helped to pave the way for today’s coordinated responsible disclosure of the new attack methodology and potential susceptibility across a multitude of common open source and commercial proxies, application servers, and load balancers.”
Vendor patches for CVE-2023-44487 are available and should be deployed as soon as possible. It is also advised to ensure that all automation like Terraform builds and images are fully patched so older versions of web servers are not deployed into production over the secure ones by accident.
As a last resort, organizations could disable HTTP/2, but that might be a bad idea for businesses that need good web performance. Prince stated, “For organizations that care about web performance, HTTP/2 remains a big win over HTTP/1.1. A lot of the responsive, app-like web (apps) that consumers have come to expect requires HTTP/2 or HTTP/3. It is possible to mitigate this attack vector and still get the benefits of a modern web protocol. So, for most businesses, turning off HTTP/2 should only be a last option.”