In August, a hacker dumped 2.7 billion data records, including social security numbers, on a dark web forum, in one of the biggest breaches in history.
The data may have been stolen from background-checking service National Public Data at least four months ago. Each record has a person’s name, mailing address, and SSN, but some also contain other sensitive information, such as names of relatives, according to Bloomberg.
This breach is related to an incident from April 8, when a known cyber-criminal group named USDoD claimed to have access to the personal data of 2.9 billion people from the U.S., U.K., and Canada and was selling the information for $3.5 million, according to a class action complaint. USDoD is thought to have obtained the database from another threat actor using the alias “SXUL.”
This data was supposedly stolen from National Public Data, also known as Jerico Pictures, and the criminal claimed it contained records for every person in the three countries. At the time, the malware website VX-Underground said this data dump does not contain information on people who use data opt-out services.
“Every person who used some sort of data opt-out service was not present,” it posted on X.
SEE: Nearly 10 Billion Passwords Leaked in Biggest Compilation of All Time
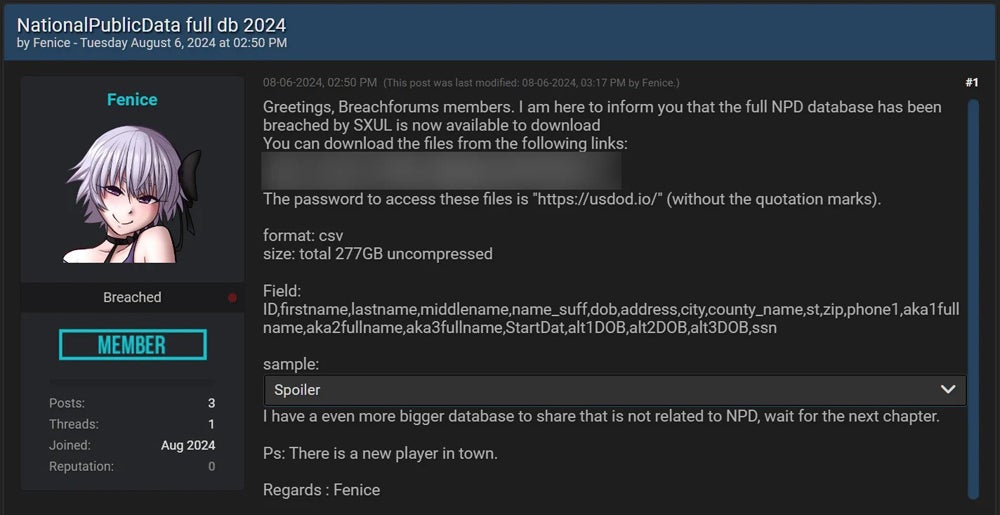
A number of cyber criminals then posted different samples of this data, often with different entries and containing phone numbers and email addresses. But it wasn’t until earlier this month that a user named “Fenice” leaked 2.7 billion unencrypted records on the dark web site known as “Breached,” in the form of two csv files totalling 277GB. These did not contain phone numbers and email addresses, and Fenice said that the data originated from SXUL.
As individuals will each have multiple records associated with them, one for each of their previous home addresses, the breach does not expose information about 2.7 billion different people. Furthermore, according to BleepingComputer, some impacted individuals have confirmed that the SSN associated with their info in the data dump is not correct.
BleepingComputer also found that some of the records do not contain the associated individual’s current address, suggesting that at least a portion of the information is out of date. However, others have confirmed that the data contained their and family members’ legitimate information, including those who are deceased.
The class action complaint added that National Public Data scrapes the personally identifying information of billions of individuals from non-public sources to create their profiles. This means that those impacted may not have knowingly provided their data. Those living in the U.S. are particularly likely to be impacted by this breach in some way.
Experts who TechRepublic spoke to suggest that individuals impacted by the breach should consider monitoring or freezing their credit reports and remain on high alert for phishing campaigns targeting their email or phone number.
Businesses should ensure any personal data they hold is encrypted and safely stored. They should also implement other security measures such as multi-factor authentication, password managers, security audits, employee training, and threat-detection tools.
SEE: How to Avoid a Data Breach
TechRepublic has reached out to Florida-based National Public Data for a response. However, it has yet to acknowledge the breach or inform impacted individuals. The existing details about the incident have been extracted from the lawsuit materials, and the company is currently under investigation by Schubert Jonckheer & Kolbe LLP.
Named plaintiff Christopher Hofmann said he received a notification from his identity-theft protection service provider on July 24 notifying him that his personal information had been compromised as a direct result of the “nationalpublicdata.com” breach and had been published on the dark web.
Jon Miller, CEO and co-founder of anti-ransomware platform Halcyon, said that the value of the National Public Data records from a criminal’s perspective comes from the fact that they have been collected and organised.
He told TechRepublic in an email, “While the information is largely already available to attackers, they would have had to go to great lengths at great expense to put together a similar collection of data, so essentially NPD just did them a favor by making it easier.”
SEE: How organizations should handle data breaches
Oren Koren, CPO and co-founder at security platform Veriti, added that information about deceased individuals could be reused for nefarious purposes. He told TechRepublic in an email, “With this ‘starting point,’ an individual can try to create birth certificates, voting certificates, etc., that will be valid due to the fact they have some of the info they need, with the most important one being the social security number.”
Paul Bischoff, consumer privacy advocate at tech research firm Comparitech, told TechRepublic in an email, “Background check companies like National Public Data are essentially data brokers who collect as much identifiable information as possible about everyone they can, then sell it to whomever will pay for it. It collects much of the data without the knowledge or consent of data subjects, most of whom have no idea what National Public Data is or does.
“We need stronger regulations and more transparency for data brokers that require them to inform data subjects when their info is added to a database, limit web scraping, and allow data subjects to see, modify, and delete data.
“National Public Data and other data brokers should be required to show data subjects where their info originally came from so that people can take proactive steps to secure their privacy at the source. Furthermore, there is no reason the compromised data should not have been encrypted.”
Miller added, “The monetization of our personal information — including the information we choose to expose about ourselves publicly — is far ahead of legal protections that govern who can collect what, how it can be used, and most importantly, what their responsibility is in protecting it.”
Chris Deibler, VP of security at security solutions provider DataGrail, said many of the cyber hygiene principles that are available for businesses and individuals would not have helped much in this instance.
He told TechRepublic in an email, “We are reaching the limits of what individuals can reasonably do to protect themselves in this environment, and the real solutions need to come at the corporate and regulatory level, up through and including a normalization of data privacy regulation via international treaty.
“The balance of power right now is not in the individual’s favor. GDPR and the various state and national regulations coming online are good steps, but the prevention and consequence models in place today clearly do not disincentivize mass aggregation of data.”