Cisco Talos analyzed the top 14 ransomware groups between 2023 and 2024 to expose their attack chain and highlight interesting Tactics,Techniques and Protocols. The security company also exposed the most leveraged vulnerabilities being triggered by ransomware actors.
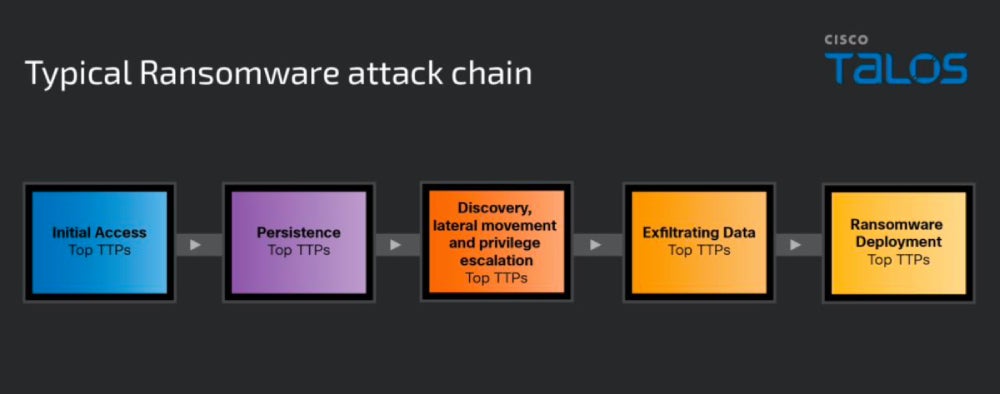
Ransomware actors nearly all use the same attack chain.
The first step for the threat actor consists of gaining access to the targeted entity. To achieve that goal, ransomware actors use different techniques — one of the most common techniques is to social engineer their targets by sending emails containing malicious files or links that will run malware on the targeted system. The malware will then allow the attacker to deploy more tools and malware to reach their goals. Multifactor authentication might be bypassed at this time using various techniques, either because of poor MFA implementation or because of owning valid credentials already.
Talos also reported that an increasing number of ransomware affiliates scan internet-facing systems for vulnerabilities or misconfigurations that could allow them to compromise the system. Unpatched or legacy software is a particularly high risk.
The second step is to gain persistence in case the initial vector of compromise gets discovered; that persistence on systems is typically achieved by modifying Windows registry keys or enabling autostart execution of the malicious code upon system boot. Local, domain and/or cloud accounts might also be created for persistence.
In the third step, the threat actor scans the network environment to get a better understanding of the inner parts of the infrastructure. Data of value that can be used for ransom is identified at this step. To successfully access all parts of the network, attackers often use tools to elevate their privileges to administrator level, in addition to using tools that allow network scanning. Popular tools for these tasks are Living Off the Land binaries AKA LOLbins, because they are executable files native to the operating system and less prone to raise alerts.
The attacker is ready to collect and steal sensitive data, which they often compress with utilities (such as 7-Zip or WinRAR) before exfiltrating the data to attacker-controlled servers by using Remote Monitoring and Management tools or more custom ones, such as StealBit or Exabyte for example, created by LockBit and BlackByte ransomware groups.
If the goal is data theft or extortion, the operation is over. If the goal is to encrypt data, the attacker needs to test the ransomware in the environment — that is, checking the delivery mechanisms and the communications between the ransomware and the C2 server — before launching it to encrypt the network and notify the victim they have been breached and need to pay the ransom.
Cisco Talos reported that three vulnerabilities on public-facing applications are commonly exploited by ransomware threat actors.
All those vulnerabilities allow ransomware actors to get initial access and manipulate systems to run more malicious payloads, install persistence or facilitate lateral movements within compromised networks.
DOWNLOAD: Cybersecurity’s Benefits and Best Practices from TechRepublic Premium
Cisco Talos observed the TTPs used by 14 of the most prevalent ransomware groups based on their volume of attack, impact to customers and atypical behavior.
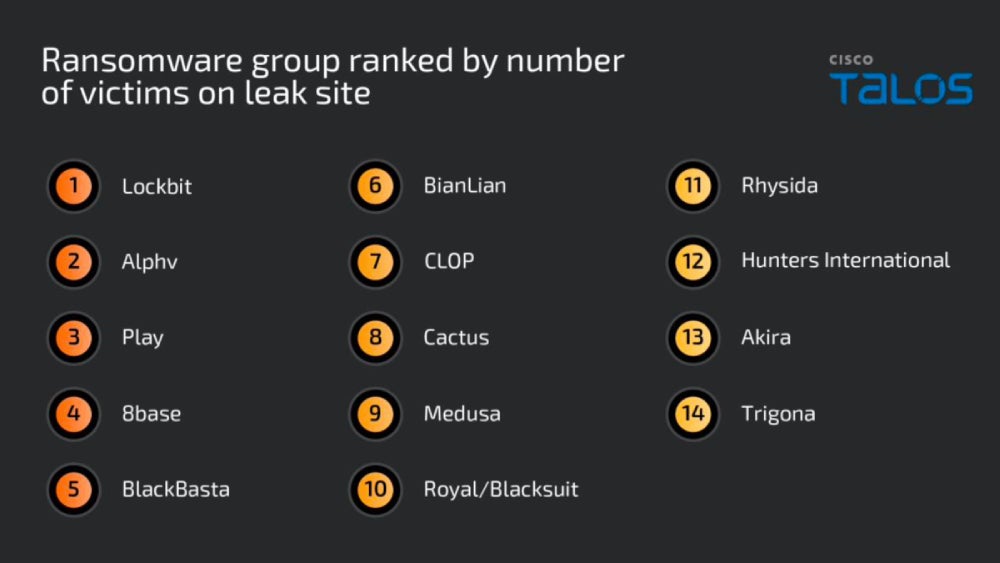
One of the key findings regarding the TTPs indicates many of the most prominent groups prioritize establishing initial compromise and evading defenses in their attack chains.
Ransomware threat actors often obfuscate their malicious code by packing and compressing it and modify the systems registry to disable security alerts on the endpoint or server. They might also block certain recovery options for the users.
The Cisco Talos researchers highlighted that the most prevalent credential access technique is the dumping of the LSASS memory contents to extract plaintext passwords, hashed passwords or authentication tokens stored in memory.
Another trend in C2 activities is the use of commercially available tools such as RMM applications. Those applications are generally trusted by the environment and allow the attacker to blend in with the corporate network traffic.
For starters, it is mandatory to apply patches and updates to all systems and software; this constant maintenance is necessary to reduce the risk of being compromised by an exploit.
Strict password policies and MFA must be implemented. Complex and unique passwords must be set for every user and MFA enforced, so an attacker possessing valid credentials is still not able to access the targeted network.
Best practices to harden all systems and environments need to be applied. Unnecessary services and features should be disabled to reduce the attack surface. Also, exposure to the internet must be reduced by limiting the number of public-facing services as much as possible.
Networks should be segmented using VLANs or similar technologies. Sensitive data and systems must be isolated from other networks to prevent lateral movements from an attacker.
Endpoints must be monitored by a Security Information and Event Management system, and Endpoint Detection and Response or Extended Detection and Response tools need to be deployed.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.