
New research from cyber security firm Rapid7 has shown the ransomware attacks that IT and security professionals are up against in APAC are far from uniform, and they would be better off tapping intelligence that sheds light on attack trends in their specific jurisdiction or sector.
Raj Samani, chief scientist at Rapid7, said actual ransomware threats often differ from assumptions based on news coverage. Attack surface research revealed significant existing vulnerabilities like open ports and storage buckets and leaked credentials, he added.
Rapid7’s research on Asia-Pacific ransomware activity, conducted during the last half of 2023, found differences based on company location and industry, indicating that organisations taking a blanket approach to ransomware defense could be missing key information.
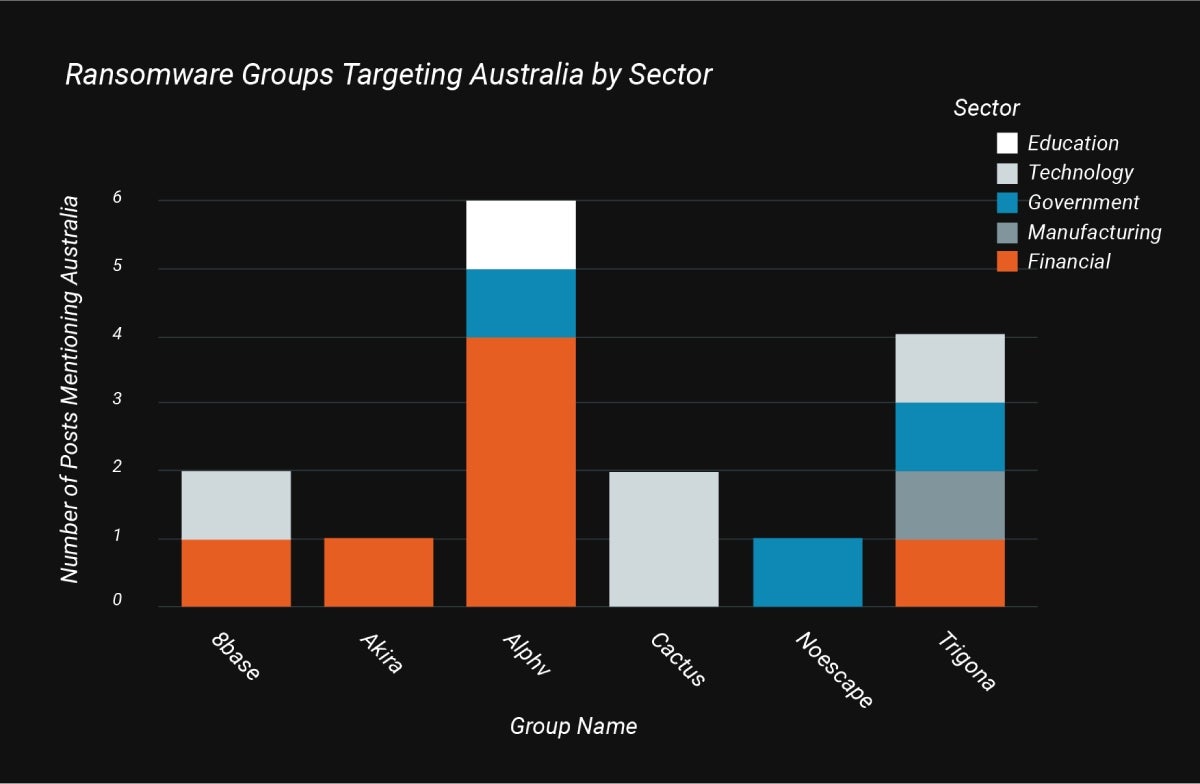
For example, the most prevalent ransomware group targeting Australia was ALPHV, or BlackCat. The group was found to be primarily targeting the financial sector, with some activity in the government and education sectors. The next biggest group was Trigona, followed by 8Base (Figure A).
Figure A
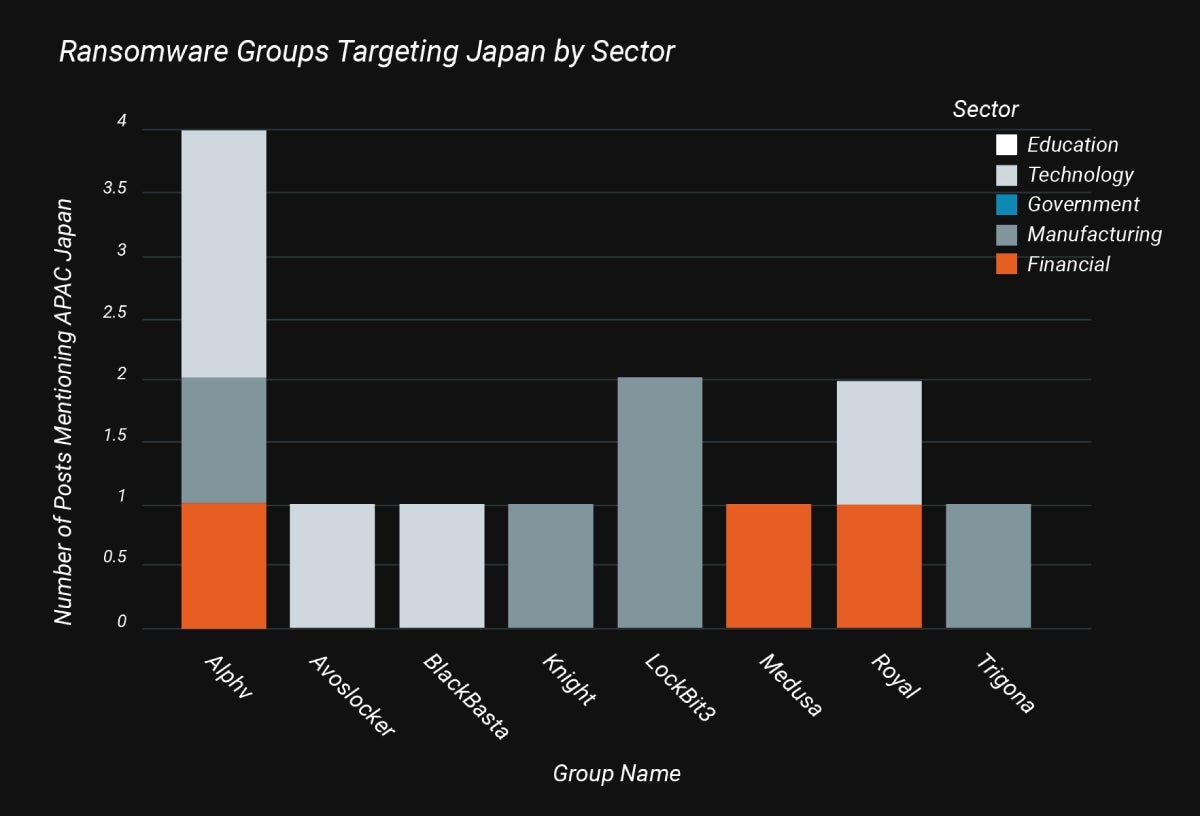
Japan was also attacked most by ALPHV, though the biggest impact was felt by the tech sector, followed by manufacturing (Figure B). The next biggest attack groups for Japan were LockBit 3.0, again targeting manufacturing, and Royal, targeting financial and technology industries.
Figure B
A side-by-side comparison of Australia with India shows that, although many threat groups appear in both countries, there are differences in the prevalence of ransomware groups in different sectors; for example, LockBit 3.0 is big in India’s financial sector but not in Australia’s (Figure C).
Figure C

Rapid7 concluded the breadth of threat groups was rather wide for regionally-targeted ransomware campaigns, but the group that is most prevalent varied based on the targeted geography or sector. “We did expect more overlap between threat actors between sectors,” Samani said.
“What was interesting was the delineation and deviation in the common threat groups in the Asia-Pacific,” Samani explained. “We can see from the data there are active ransomware groups specifically going after individual sectors or specific countries across APAC.”
Samani added that, while a CISO in Indonesia, Malaysia or China might be hearing a lot about LockBit or ALPHV, there may be other ransomware threat groups to worry about. “There are multiple other threat groups that are hugely successful going completely under the radar no one talks about.”
A concerning finding was how open organisations are to ransomware attacks. “We looked at the attack surface of sectors within markets like Australia, and asked if attackers were going to do recon and break inside for a ransomware attack, is this something that is easy to do?”
Rapid7 found that, while “the windows and doors” were not being left open for attackers, they were being left “unlocked.” Samani cited the number of open ports and storage buckets, the access to and availability of leaked credentials, as well as unpatched systems in the region.
“These things are not glamorous or exciting. But by looking at whether you have open or test systems on the internet, or storage buckets are locked down, you are starting to make it difficult for access brokers, who are skilled at getting access and selling that on to threat groups.”
Rapid7’s analysis used machine learning to analyse the external access surface of multiple sectors within the APAC region over the last half of 2023. It processed data available “beyond openRDP and unpatched systems,” including leak sites and compromised datasets.
Ransomware attacks are on the rise in Asia-Pacific. A recent report from Group-IB found that, based on companies with information published on ransomware data leak sites, regional attacks increased by 39% to a total of 463, with the most (101) occurring in Australia.
SEE: Cyber Security Trends to Watch in Australia in 2024
Rapid7 recommends organisations in the Asia-Pacific take a more intelligence-based, nuanced approach to dealing with ransomware risk. Samani said they should not be prioritising or “speculating based on headlines involving organisations halfway across the globe.”
“Everyone talks about the same ransomware families. But no one has sat down to look and say, ‘Well, that doesn’t really apply here, what applies here is this group,’” Samani explained.
The firm argues that combining external attack surface management and actionable intelligence to identify assets with vulnerabilities being exploited in the wild should take the highest priority, especially when an attributed ransomware campaign is targeting the sector or geography of the organisation.
“Getting that visibility and intelligence is crucial,” Samini said. “That level of intelligence means you know who you are up against, and how to protect yourself.”