
Credentials are the achilles heel in enterprise security, according to a new report from Google Cloud’s Cybersecurity Action Team, which found that credential vulnerabilities accounted for 60% of compromise factors among Google Cloud users. The company’s security group said, in its new Threat Horizons Report, that hardening these soft spots can be achieved with basic attention to zero-trust details, including strong identity management guardrails.
Additionally, the Google Cloud team reported that misconfiguration problems accounted for 19% of compromise factors, which were also associated with other compromise factors such as application programming interfaces or sensitive user interfaces exposed to the wild by snafus like misconfigured firewalls (Figure A).
Figure A
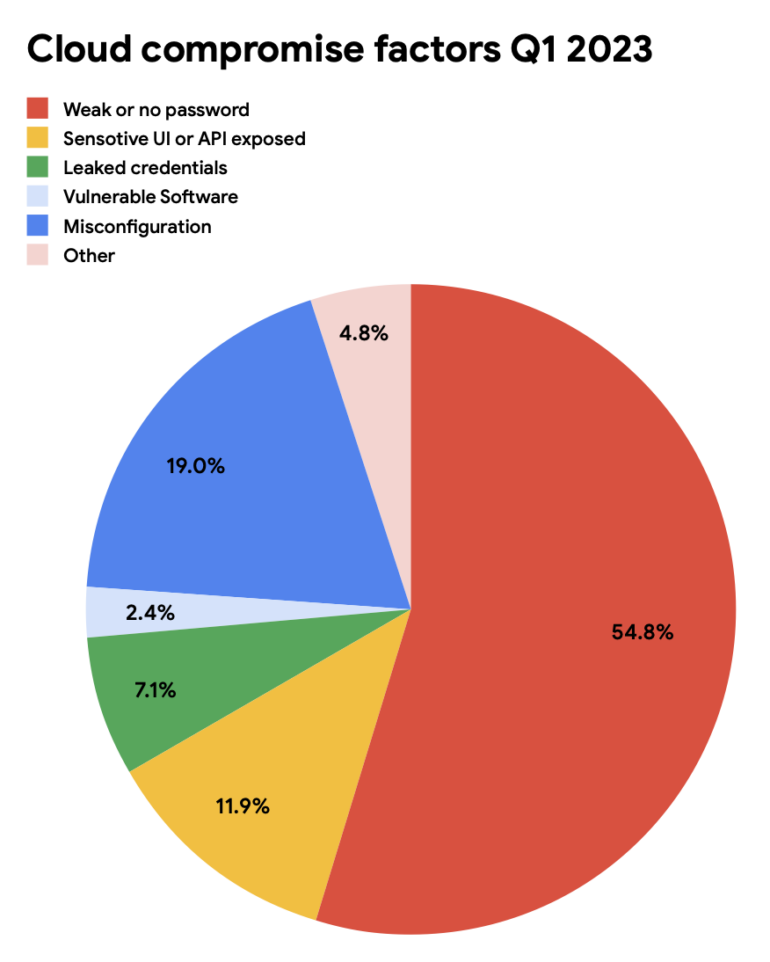
“Every quarter we see the same activities, but attackers are getting more sophisticated in how they implement these,” said Matt Shelton, head of threat research and analysis at Google Cloud. “We continue to see IAM as the number one problem and I suspect we will continue to see that over the next several quarters. Stolen account credentials and misconfigurations are what everyone’s going after these days,” he added.
Jump to:
In the report designed for enterprise users of Google Cloud, the team analyzed anonymized first quarter, 2023 alert statistics from Chronicle, Google’s software-as-a-security suite for security operations centers, to identify compromise-inducing risk factors.
The predominant alerts in the first quarter of 2023, constituting nearly 75% of alerts, were for cross-project abuse of access token generation permissions. Broadly speaking, this is a problem of privilege access management, frequently involving over-provisioned accounts, where IT teams look to increase uptime and reduce complexity by granting too much access to accounts, violating the concept of least privilege.
Shelton pointed out that over-provisioned accounts are common with cross-project identity access, explaining that a user very typically creates a service account with too many permissions, in order to facilitate work. The attacker then steals those credentials and attempts to take such actions as accessing a different project or escalating privileges.
“Over-provisioned accounts usually apply to service or privileged admin accounts, so the consequence of the stolen ID is worse than if it were an end user account,” Shelton said.
One example of an over-provisioning misstep is the over use of secure shell keys, which provide access to encrypted secure shell network protocols designed to let machines communicate on an unsecured open network. SSH keys are used to perform remote actions such as file transfers, network management and accessing operating systems.
“If I am an admin logging into a GCP Linux instance I have a private key on my endpoint that a bad guy can steal, and use it to log in. That’s an attack vector that has been around for years and years. We have evolved beyond that, but it’s still widely used in the industry, as our report shows,” Shelton said. “It is yet another identity store you need to keep track of. No one puts an SSH key on a low priority system, it’s always on the back end Unix system that holds sensitive data,” he said. (Figure B).
Figure B
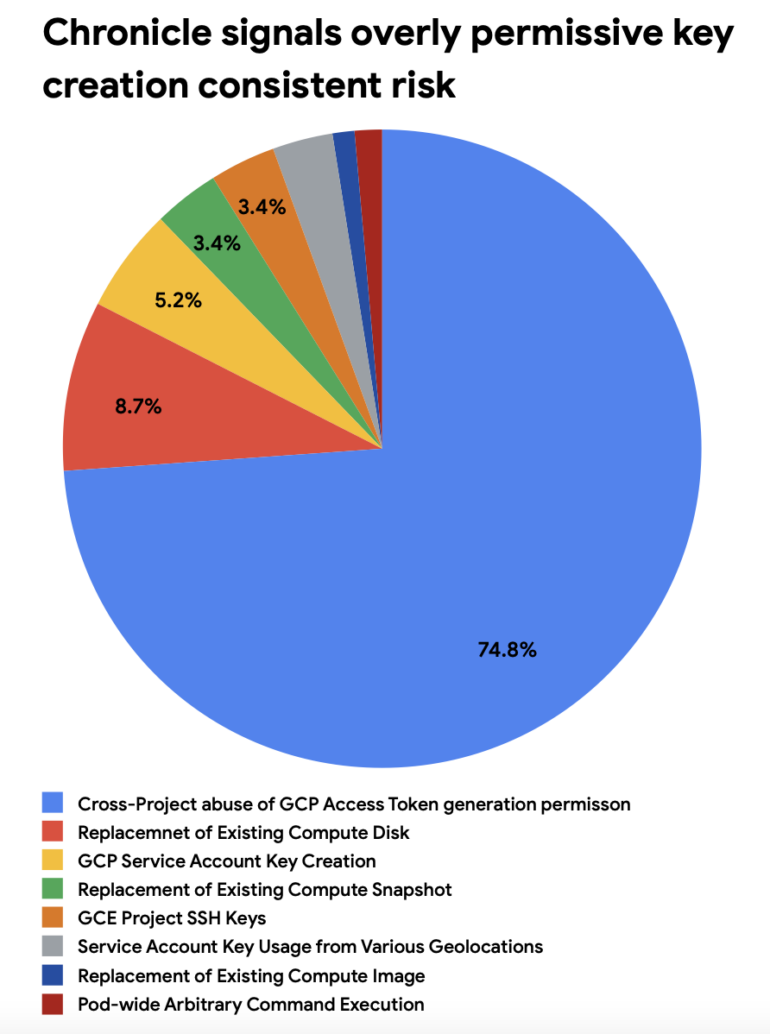
Shelton said a better tactic is to use the username and password that comes with the Google IAM tool. “This is zero trust. It ensures you have one account, one password with multi-factor authentication, a central location where you can disable or re-enable it and a central place to look at the logs. So our recommendation is, yes, IAM is one of the key compromise vectors but there are tools based off zero-trust principles that can help you protect your account,” he said.
The Google Cloud Security group offered key suggestions for improving identity management hygiene:
Researchers also identified instances of Android applications attempting to evade Google Play Store’s malware detections before downloading malware. This tactic, called “versioning,” involves a version of an app that gains the Play Store’s trust before issuing a malicious update of that same application. Google Cloud’s report cited the SharkBot malware variant, a banking malware that initiates money transfers from compromised devices using the Automated Transfer Service protocol.
The variants of SharkBot that appeared on Google Play had reduced functionality, a cloaking technique that makes suspicious apps harder to detect, according to Shelton.
“Versioning is a big deal. Google has invested a lot of time and effort into reviewing apps in Google Play store,” Shelton said. “What tends to happen is an app gets published out to Google Play store. It gets reviewed, it’s completely benign and there’s no malware in it whatsoever. Then, using … versioning, after it is installed on a user device, usually as, say, a game, or consumer tool, and accesses a third-party site, [the app] downloads malicious code after the app determines the user is a valuable target, and performs malice,” he added.
He said this is a problem not only for individuals but also for enterprises. The apps not only steal money and conduct financial transactions, but they can also steal information.
“That keeps me up at night because people are logging into work accounts from their personal phones, and these info stealers will grab credentials from that phone and send them to an attacker. And that goes right back to the narrative around stolen credentials being key, not just on cloud but on mobile,” Shelton said.
Google’s report also looked at DevOps vulnerabilities in the continuous integration/development process, noting that credential and authentication token compromise are often factors in source code incidents.
“There have been cases in which a compromise of a third-party service involved in hosting the code or the continuous integration/continuous development process led to compromises of users of these services, as well as malicious insider incidents and misconfigurations,” according to the study.
Shelton said focusing on zero-trust protocols and defense-in-depth principals can go a long way in blocking attackers at the root.
“What this report shows is that, just as we have done [on premise] for years and years, in the cloud we have to practice defense in depth — we have to layer in detection strategies and take a look at the whole threat landscape. You need to assume compromise at all times and build a security strategy with several layers,” he said.
Shelton also said a major takeaway from the report is that even as attackers get more sophisticated, particularly around a major attack magnet — credentials and exploitation of IAM vulnerabilities generally — zero-trust protocols are critical.
“It comes down to cyber hygiene. Today, you have to practice fundamentals perfectly,” he said. “We talk quite a bit about sophisticated attacks, but at the end of the day, an adversary only needs to do the bare minimum to help them achieve their objectives.”