In a sweeping international effort, the U.S. Department of Justice, the Federal Bureau of Investigation, and multiple global law enforcement agencies have exposed “Operation Magnus,” targeting two of the world’s most notorious information-stealing malware networks, RedLine Stealer and META.
According to a press release published on Oct. 29, the operation led to the seizure of multiple servers, the unsealing of charges against a RedLine Stealer developer, and the arrest of two suspects in Belgium.
RedLine Stealer and META are two distinct types of malware known as “information stealers,” or “infostealers,” designed to capture sensitive user data. The existence of RedLine Stealer was initially reported in 2020, while META first appeared in 2022.
In an interview, a representative of the META malware revealed that its development initially relied on portions of RedLine Stealer’s source code, which had been acquired through a sale. Both malware are capable of stealing sensitive information from infected computers, such as:
SEE: How to Create an Effective Cybersecurity Awareness Program (TechRepublic Premium)
Both malware also provide the capability to bypass multi-factor authentication. The stolen information can be used by the controller of the malware but can also be sold as files called “logs” in underground cybercriminal forums or marketplaces.
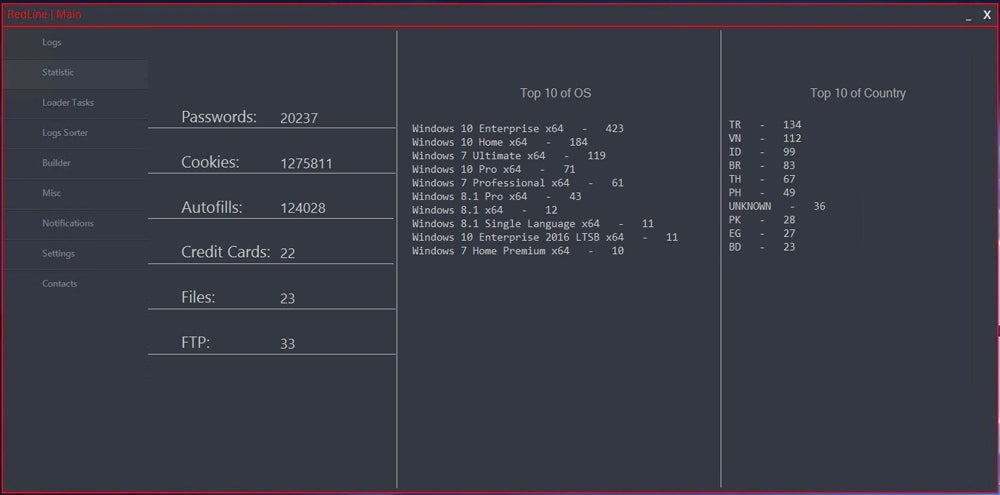
RedLine Stealer and META have infected millions of computers worldwide — and have stolen even more credentials. Specops Software, a company focused on password security, reported that RedLine Stealer captured more than 170 million passwords in only six months, while META stole 38 million passwords during that same period.
RedLine Stealer has also been used to conduct intrusions against major corporations, according to the DOJ press release.
Both malware families are sold through a Malware-as-a-Service business model, where cybercriminals purchase a license to use variants of the malware and then launch their own infecting campaigns. This can be done via infecting emails, malvertising, fraudulent software downloads, malicious software sideloading, and instant messaging. Different cybercriminals have used various social engineering lures and tricks to infect victims, including fake Windows updates.
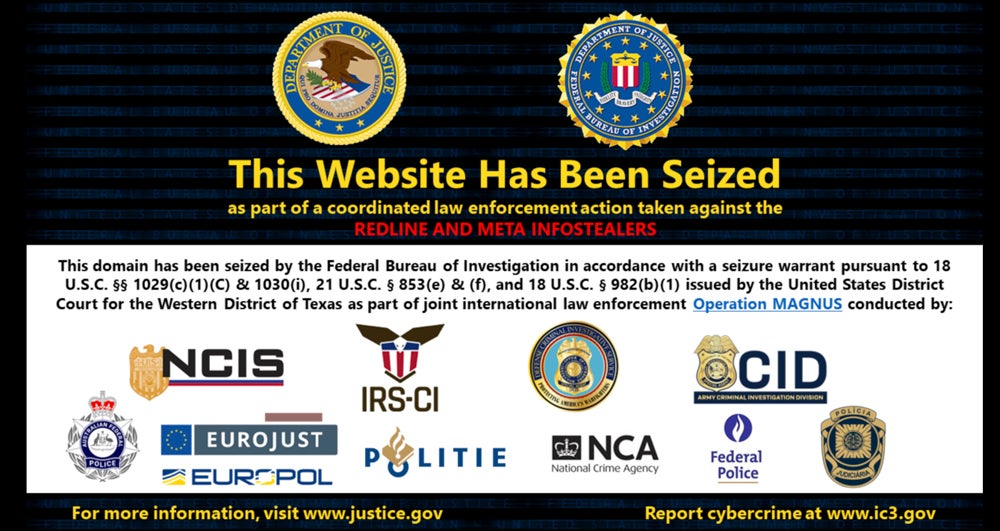
A warrant issued by the Western District of Texas authorized law enforcement to seize two command and control domains used by RedLine Stealer and META.
Both domains now show content about the operation.
Three servers have been shut down in the Netherlands, and several RedLine Stealer and META communication channels have been taken down by Belgian authorities.
Additionally, a website about Operation Magnus informs and supports victims. A video shown on the website sends a strong message to cybercriminals who have used RedLine or META, exposing a list of nicknames said to be VIPs — “Very Important to the Police” — and ends with the image of handcuffs and a message: “We are looking forward to seeing you soon!”
The website also offers an online scanner for RedLine/META infections from cybersecurity company ESET.
The U.S. DOJ has also unsealed charges against Maxim Rudometov, one of the developers and administrators of the RedLine Stealer malware, who regularly accessed and managed the infrastructure. Rudometov is also associated with various cryptocurrency wallets used to receive and launder payments from RedLine customers.
Two other individuals were also taken into custody in Belgium, although one was released without further details available to the public.
Information stealers can infect computers in myriad ways — which is why all systems and software must be updated and patched to prevent an infection that would leverage a common vulnerability.
In addition:
Further, users should never use the same password for different services. The use of password managers is highly efficient to use a single complex password for every service or tool and should be mandatory in organizations.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.