A new joint cybersecurity advisory from the Federal Bureau of Investigation, the Cybersecurity and Infrastructure Security Agency, and the Department of Defense Cyber Crime Center exposed new information about the infamous Iran-based threat actor known as Fox Kitten.
The group sells the corporate access they obtain in cybercriminal’s underground forums and collaborates actively with ransomware affiliates to assist in ransoming victims. The threat actor has set their sights on infiltrating the U.S. and other foreign organizations in recent weeks.
Fox Kitten — also known as Pioneer Kitten, UNC757, Parasite, Rubidium, and Lemon Sandworm — is a threat actor that has actively committed cyberespionage since at least 2017.
The FBI said that the group is associated with the Iranian government and supports the theft of sensitive technical data against various organizations, per the advisory. The threat actor has targeted companies in the middle-east such as Israel and Azerbaijan, but also companies in Australia, Finland, Ireland, France, Germany, Algeria, Turkey, the U.S., and possibly more.
According to the advisory, Fox Kitten has conducted a high volume of computer network intrusion attempts against U.S. organizations since 2017. Their targets have included U.S.-based schools, municipal governments, financial institutions, and healthcare facilities, with incidents as recent as August 2024.
OT cybersecurity company Dragos noted that the threat actor also targeted ICS-related entities by exploiting vulnerabilities in Virtual Private Network appliances.
The advisory also revealed that the group uses “the Iranian company name Danesh Novin Sahand (identification number 14007585836), likely as a cover IT entity for the group’s malicious cyber activities.”
In 2020, operation “Pay2Key,” led by Fox Kitten, showed that the threat actor could follow other goals rather than just facilitating cyberespionage.
According to Israeli-based company ClearSky Cyber Security, ransomware attacks targeted Israeli organizations with previously unreported ransomware, yet the attack campaign was likely propaganda to cause fear and create panic in Israel. Data stolen during the attacks was exposed publicly on a leak site that mentioned “Pay2Key, Israel cyberspace nightmare!” as shown in the report.
Another report, published by cybersecurity company CrowdStrike in 2020, revealed that the threat actor also advertised to sell access to compromised networks on an underground forum. Researchers consider this activity as a potential attempt at revenue stream diversification, alongside the targeted intrusions in support of the Iranian government.
Once Fox Kitten has obtained access to victim networks, the group collaborates with a few ransomware affiliates from the NoEscape, RansomHouse, and ALPHV/BlackCat. The threat actor provides full access to ransomware affiliates in exchange for a percentage of the ransom payments.
Fox Kitten provides more than just access to compromised networks, according to the FBI. The group works closely with the ransomware affiliates to lock victim networks and strategize approaches to extort victims. Yet the group does not reveal its Iran-based location to their ransomware affiliate contacts and stays vague as to their origin.
The joint advisory reveals that the group refers to themselves by the moniker “Br0k3r” and has used “xplfinder” in their channels in 2024.
Fox Kitten uses the Shodan search engine to identify IP addresses hosting devices vulnerable to specific exploits, such as Citrix Netscaler, F5 Big-IP, Pulse Secure/Ivanti VPNs, or PanOS firewalls.
Once the vulnerabilities are exploited, the threat actor:
The joint advisory provides several indicators of compromise but also lists the TOX identifiers for the moniker “Br0k3r.” TOX is a peer-to-peer instant messaging software designed to provide secure communications and uses unique keys to identify users.
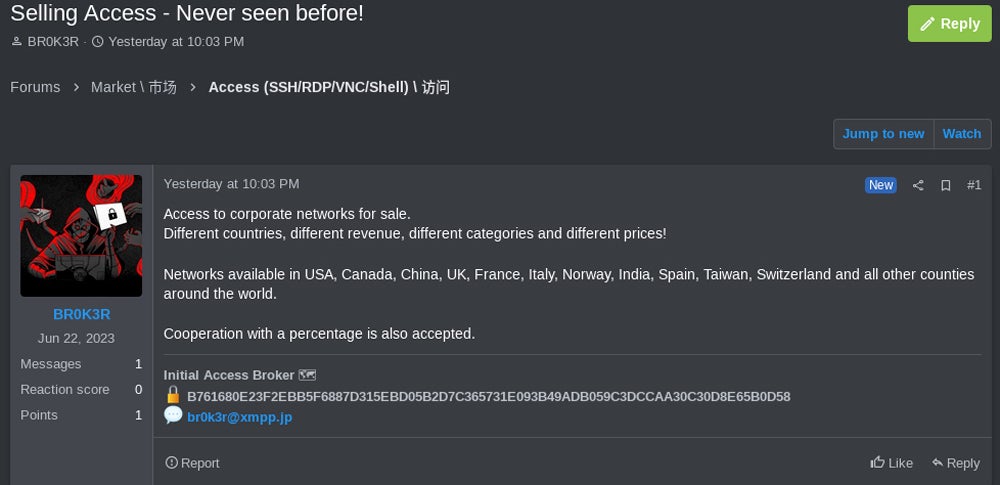
The unique TOX ID for “Br0k3r” has already been exposed in 2023 by the SANS Institute as an Initial Access Broker selling access to corporate networks in different countries, including the U.S., Canada, China, the U.K., France, Italy, Norway, Spain, India, Taiwan, and Switzerland.
It is no surprise to see the threat actor target the U.S., as it is the most ransomware-impacted country according to cybersecurity company MalwareBytes.
The threat actor provided a unique Tor-hosted website to advertise their access on several different cybercriminal’s forums.
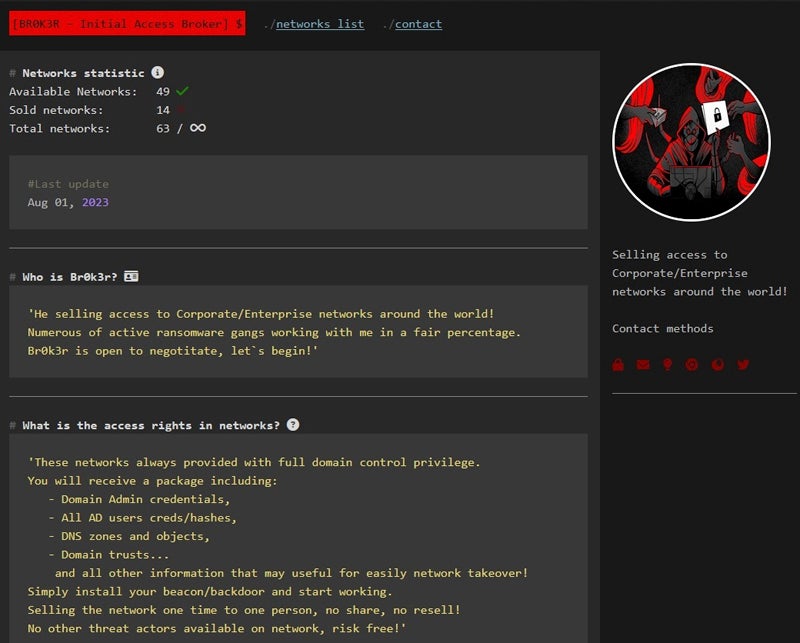
A first version of Br0k3r’s website indicates that every sale contains full-domain control, including domain admin credentials, Active Directory user credentials, DNS zones and objects, and Windows Domain trusts.
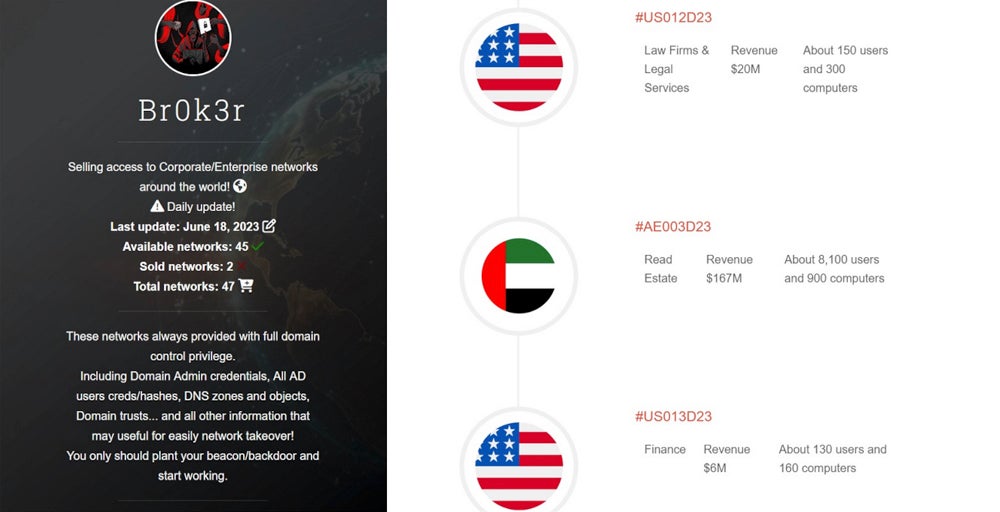
A second version of the website launched around August 2023 indicates “Numerous active ransomware gangs working with me in a fair percentage.”
The initial compromise method deployed by Fox Kitten consists of exploiting known vulnerabilities in several different Internet-facing appliances, in particular corporate VPNs or firewall appliances. To protect from this cyber threat, companies should:
Finally, the FBI and the CISA do not recommend paying the ransom, as there is no guarantee that victims will recover their encrypted files, and those payments might also fund other criminal activities.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.